Destroying Infrastructure with Pipelines
This tutorial will help you learn how to destroy infrastructure using Gruntwork Pipelines and GitOps workflows.
What you'll get
By the end, you'll have:
- Destroyed cloud resources (AWS or Azure) using Gruntwork Pipelines
Prerequisites
Before starting, make sure you have:
- Pipelines installed in a GitHub/GitLab repository. Refer to Setup & Installation for details.
- Access to a sandbox or development cloud environment (AWS account or Azure subscription) configured during the Pipelines installation process.
- Permissions to create a pull/merge request in the GitHub/GitLab repository where Pipelines is installed.
- An existing cloud resource created using Infrastructure as Code (IaC) and Pipelines that you want to destroy. If no resource exists, follow the steps in the Deploying your first infrastructure change tutorial to create one, which will then be destroyed in this tutorial.
Destroying with pipelines
This section explains how to destroy cloud resources using Pipelines and GitOps workflows. The example used is the resources created in the Deploying your first infrastructure change tutorial, but the process applies to any resource you wish to destroy.
Delete the infrastructure code
- AWS
- Azure
By default, Pipelines is configured with the permissions needed to complete this tutorial. However, depending on your specific setup, you may need to adjust the IAM roles used by Pipelines to ensure they have the necessary permissions to destroy resources.
The default Pipelines role has permissions to delete S3 buckets with names that start with test-pipelines-. If you're destroying resources with different naming conventions, you may need to update the IAM policy accordingly.
The default bootstrap Terragrunt stack provided in the installation guide includes plan_iam_policy and apply_iam_policy values that can be configured to adjust the permissions granted to Pipelines.
:::
-
Remove the folder containing the infrastructure code for the resource you want to destroy. For the S3 bucket example, delete the folder containing the S3 bucket code. Replace <ACCOUNT_NAME> and <REGION> with the appropriate values.
rm -rf <ACCOUNT_NAME>/<REGION>/data-storage/s3 -
Create a new branch, commit the changes, and push the branch to your repository.
By default, Pipelines is configured with the permissions needed to complete this tutorial. However, depending on your specific setup, you may need to adjust the role used by Pipelines to ensure it has the appropriate permissions to delete Resource Groups and Storage Accounts in your subscription.
The default bootstrap Terragrunt stack provided in the installation guide includes plan_custom_role_actions and apply_custom_role_actions values that can be configured to adjust the permissions granted to Pipelines.
:::
-
Remove the folder containing the infrastructure code for the resources you want to destroy. For the Resource Group and Storage Account example, delete the folder containing all the resource group code. Replace <SUBSCRIPTION_NAME>, <LOCATION>, and <RESOURCE_GROUP_NAME> with the appropriate values.
rm -rf <SUBSCRIPTION_NAME>/<LOCATION>/resource-groups/<RESOURCE_GROUP_NAME> -
Create a new branch, commit the changes, and push the branch to your repository.
Planning the destruction
- GitHub
- GitLab
Create a Pull Request (PR) for the branch you just pushed, targeting main (the default branch in your repository).
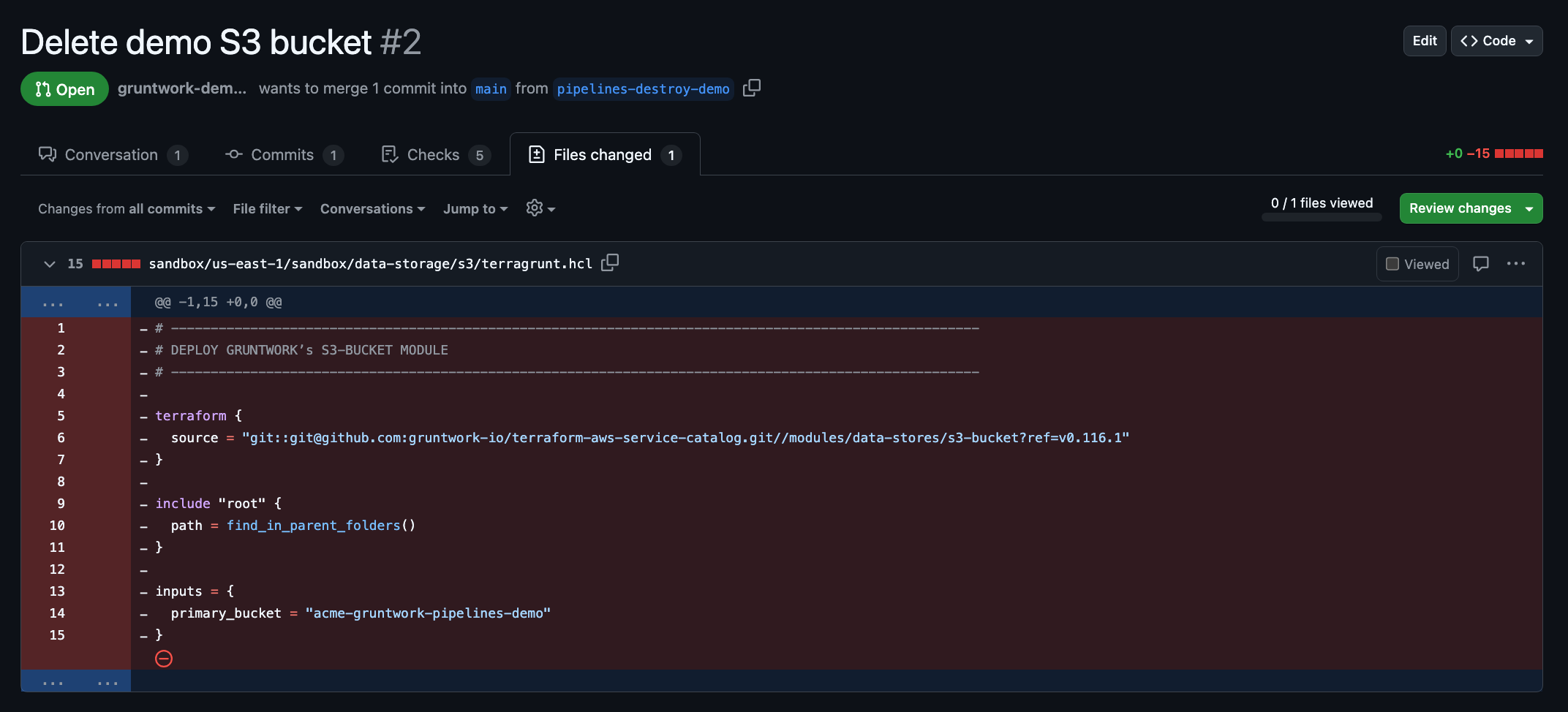 Delete Infrastructure Code
Delete Infrastructure Code
Gruntwork Pipelines, via GitHub Actions, will detect the removal of the infrastructure unit's code and trigger a plan action in Pipelines. This action will display the destructive changes to be made to your cloud environment.
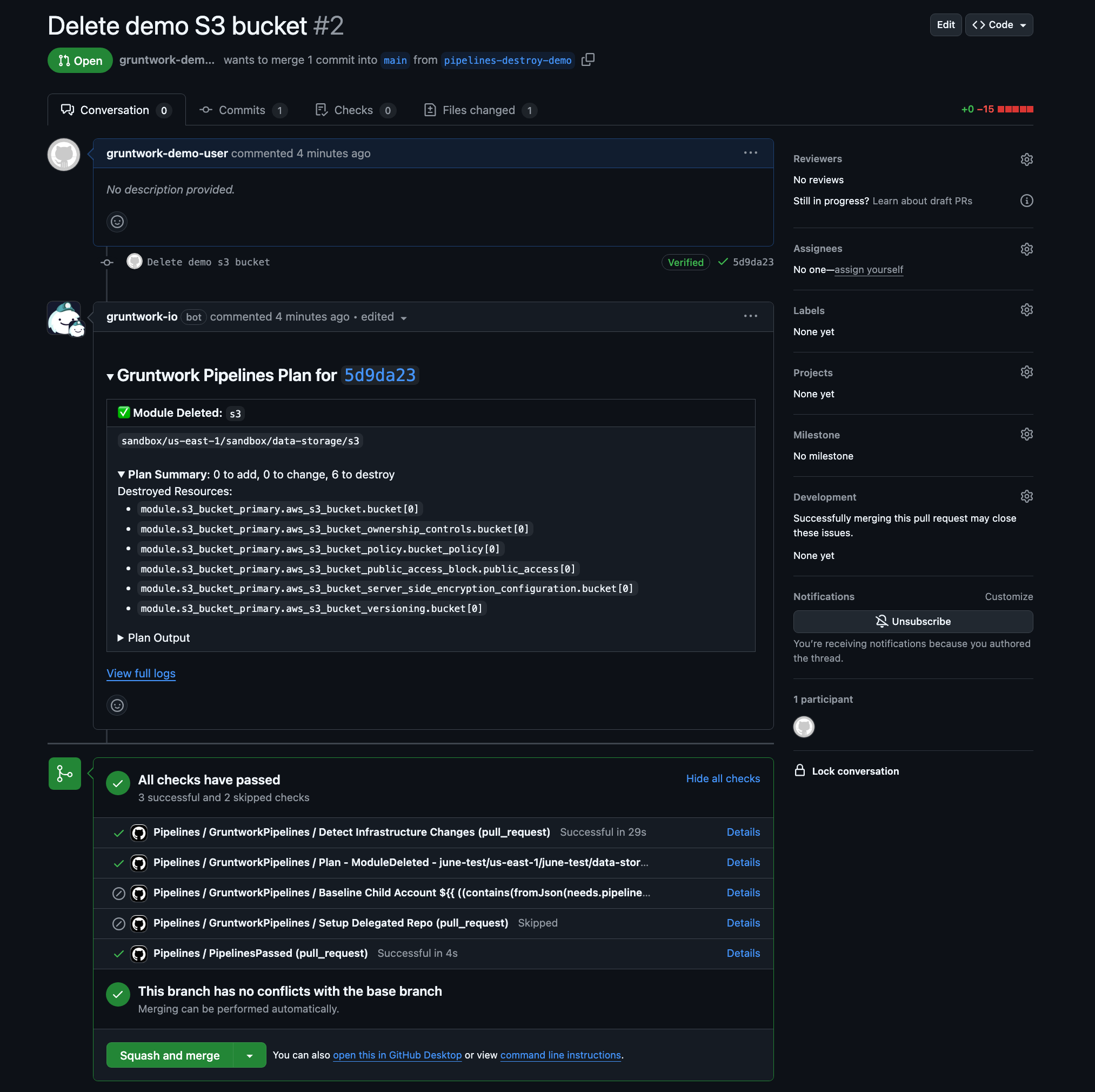 Pipelines Destroy Plan Comment
Pipelines Destroy Plan Comment
Create a Merge Request (MR) for the branch you just pushed, targeting main (the default branch in your project).
Gruntwork Pipelines, via GitLab CI/CD, will detect the removal of the infrastructure unit's code and trigger a plan action in Pipelines. This action will display the destructive changes to be made to your cloud environment.
Click the View Pipeline Logs link to see the complete output of the destroy plan.
Applying the destruction
If you are satisfied with the changes shown in the plan action, you can proceed to destroy the resources.
Approve and merge the pull/merge request to trigger the apply action, permanently deleting the resources from your cloud environment.
Congratulations! You have successfully destroyed cloud resources using Gruntwork Pipelines and GitOps workflows.
- AWS
- Azure
To verify the S3 bucket has been destroyed, check the AWS Management Console and confirm the bucket no longer exists in the S3 service.
To verify the Resource Group and Storage Account have been destroyed, visit the Azure Portal and confirm the Resource Group no longer exists.