Amazon ECR Repositories
Overview
This service contains code to create and manage multiple Amazon Elastic Container Repository (ECR) Repositories that can be used for storing and distributing container images.
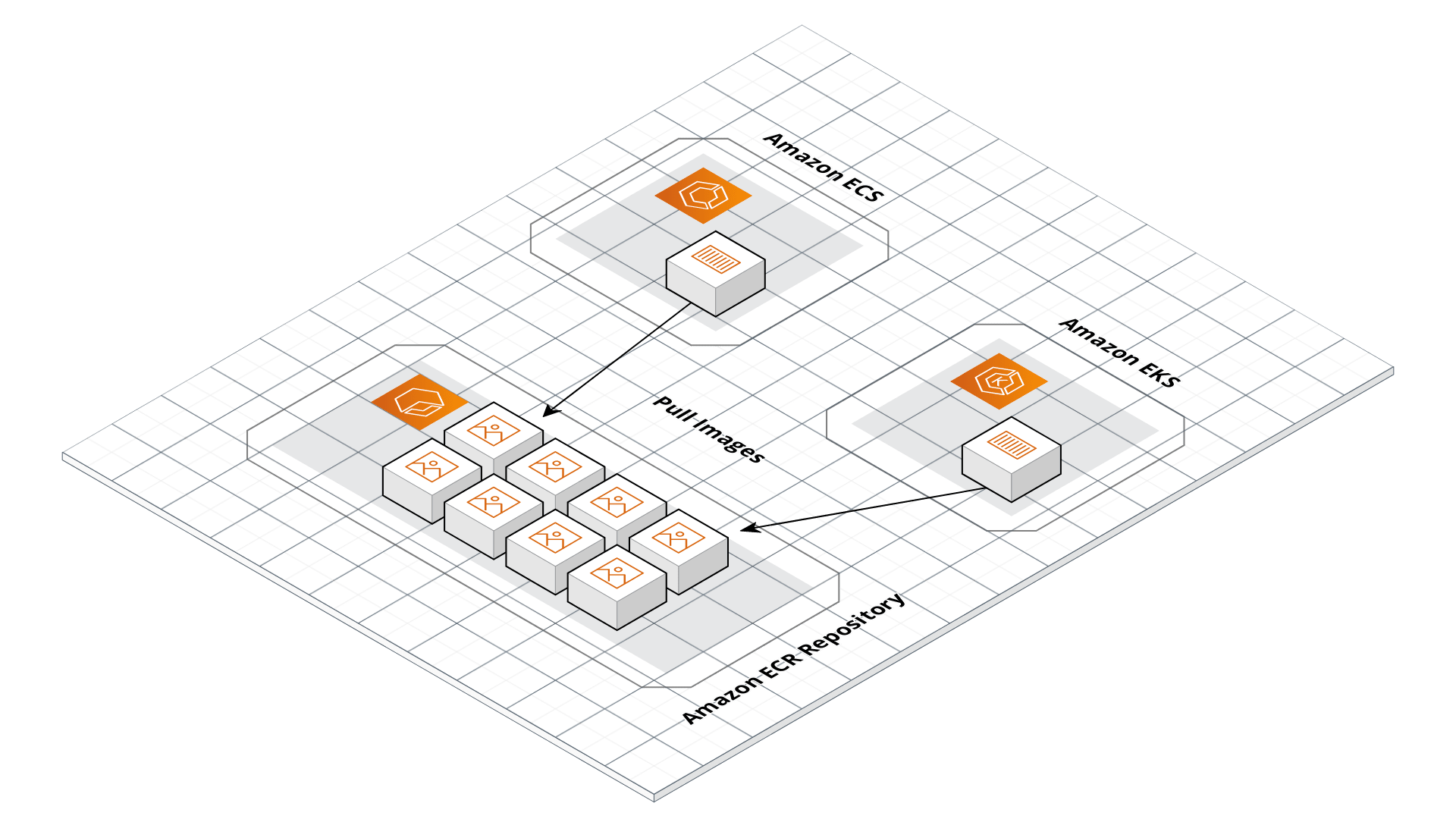 ECR architecture
ECR architecture
Features
- Create and manage multiple ECR repositories
- Store private Docker images for use in any Docker Orchestration system (e.g., Kubernetes, ECS, etc)
- Share repositories across accounts
- Fine grained access control
- Default deny ECR permissions
- Automatically scan Docker images for security vulnerabilities
Learn
This repo is a part of the Gruntwork Service Catalog, a collection of reusable, battle-tested, production ready infrastructure code. If you’ve never used the Service Catalog before, make sure to read How to use the Gruntwork Service Catalog!
- ECR documentation: Amazon’s docs for ECR that cover core concepts such as repository URLs, image scanning, and access control.
Deploy
Non-production deployment (quick start for learning)
If you just want to try this repo out for experimenting and learning, check out the following resources:
- examples/for-learning-and-testing folder: The
examples/for-learning-and-testingfolder contains standalone sample code optimized for learning, experimenting, and testing (but not direct production usage).
Production deployment
If you want to deploy this repo in production, check out the following resources:
- examples/for-production folder: The
examples/for-productionfolder contains sample code optimized for direct usage in production. This is code from the Gruntwork Reference Architecture, and it shows you how we build an end-to-end, integrated tech stack on top of the Gruntwork Service Catalog.
Sample Usage
- Terraform
- Terragrunt
# ------------------------------------------------------------------------------------------------------
# DEPLOY GRUNTWORK'S ECR-REPOS MODULE
# ------------------------------------------------------------------------------------------------------
module "ecr_repos" {
source = "git::git@github.com:gruntwork-io/terraform-aws-service-catalog.git//modules/data-stores/ecr-repos?ref=v1.3.0"
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
# ----------------------------------------------------------------------------------------------------
# A map of repo names to configurations for that repository.
repositories = <any>
# ----------------------------------------------------------------------------------------------------
# OPTIONAL VARIABLES
# ----------------------------------------------------------------------------------------------------
# Whether or not to enable image scanning on all the repos. Can be overridden
# on a per repo basis by the enable_automatic_image_scanning property in the
# repositories map.
default_automatic_image_scanning = true
# The default encryption configuration to apply to the created ECR repository.
# When null, the images in the ECR repo will not be encrypted at rest. Can be
# overridden on a per repo basis by the encryption_config property in the
# repositories map.
default_encryption_config = {"encryption_type":"AES256","kms_key":null}
# The default list of AWS account IDs for external AWS accounts that should be
# able to create Lambda functions based on container images in these ECR
# repos. Can be overridden on a per repo basis by the
# external_account_ids_with_lambda_access property in the repositories map.
default_external_account_ids_with_lambda_access = []
# The default list of AWS account IDs for external AWS accounts that should be
# able to pull images from these ECR repos. Can be overridden on a per repo
# basis by the external_account_ids_with_read_access property in the
# repositories map.
default_external_account_ids_with_read_access = []
# The default list of AWS account IDs for external AWS accounts that should be
# able to pull and push images to these ECR repos. Can be overridden on a per
# repo basis by the external_account_ids_with_write_access property in the
# repositories map.
default_external_account_ids_with_write_access = []
# The tag mutability setting for all the repos. Must be one of: MUTABLE or
# IMMUTABLE. Can be overridden on a per repo basis by the image_tag_mutability
# property in the repositories map.
default_image_tag_mutability = "MUTABLE"
# Add lifecycle policy to ECR repo.
default_lifecycle_policy_rules = []
# Whether or not to enable strict deny rules on repo, including deny on change
# repo policy. Can be overridden on a per repo basis by the strict_deny_rules
# property in the repositories map.
default_strict_deny_rules_enabled = false
# The default list of users or roles that should be able to perform functions
# on these ECR repos. All other users and roles are to be forbidden.
# Formatted as 21 letters or numbers: AROAXXXXXXXXXXXXXXXXX or
# AIDAXXXXXXXXXXXXXXXXX -
# https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-unique-ids.
# Can be overridden on a per repo basis by the
# users_or_roles_to_allow_deny_all_else property in the repositories map.
default_users_or_roles_to_allow_deny_all_else = []
# A map of tags (where the key and value correspond to tag keys and values)
# that should be assigned to all ECR repositories.
global_tags = {}
# values to filter on when replicating the ECR repository to other regions.
# See
# https://docs.aws.amazon.com/AmazonECR/latest/userguide/registry-settings-examples.html
# for example values.
replication_filters = []
# List of regions (e.g., us-east-1) to replicate the ECR repository to.
replication_regions = []
}
# ------------------------------------------------------------------------------------------------------
# DEPLOY GRUNTWORK'S ECR-REPOS MODULE
# ------------------------------------------------------------------------------------------------------
terraform {
source = "git::git@github.com:gruntwork-io/terraform-aws-service-catalog.git//modules/data-stores/ecr-repos?ref=v1.3.0"
}
inputs = {
# ----------------------------------------------------------------------------------------------------
# REQUIRED VARIABLES
# ----------------------------------------------------------------------------------------------------
# A map of repo names to configurations for that repository.
repositories = <any>
# ----------------------------------------------------------------------------------------------------
# OPTIONAL VARIABLES
# ----------------------------------------------------------------------------------------------------
# Whether or not to enable image scanning on all the repos. Can be overridden
# on a per repo basis by the enable_automatic_image_scanning property in the
# repositories map.
default_automatic_image_scanning = true
# The default encryption configuration to apply to the created ECR repository.
# When null, the images in the ECR repo will not be encrypted at rest. Can be
# overridden on a per repo basis by the encryption_config property in the
# repositories map.
default_encryption_config = {"encryption_type":"AES256","kms_key":null}
# The default list of AWS account IDs for external AWS accounts that should be
# able to create Lambda functions based on container images in these ECR
# repos. Can be overridden on a per repo basis by the
# external_account_ids_with_lambda_access property in the repositories map.
default_external_account_ids_with_lambda_access = []
# The default list of AWS account IDs for external AWS accounts that should be
# able to pull images from these ECR repos. Can be overridden on a per repo
# basis by the external_account_ids_with_read_access property in the
# repositories map.
default_external_account_ids_with_read_access = []
# The default list of AWS account IDs for external AWS accounts that should be
# able to pull and push images to these ECR repos. Can be overridden on a per
# repo basis by the external_account_ids_with_write_access property in the
# repositories map.
default_external_account_ids_with_write_access = []
# The tag mutability setting for all the repos. Must be one of: MUTABLE or
# IMMUTABLE. Can be overridden on a per repo basis by the image_tag_mutability
# property in the repositories map.
default_image_tag_mutability = "MUTABLE"
# Add lifecycle policy to ECR repo.
default_lifecycle_policy_rules = []
# Whether or not to enable strict deny rules on repo, including deny on change
# repo policy. Can be overridden on a per repo basis by the strict_deny_rules
# property in the repositories map.
default_strict_deny_rules_enabled = false
# The default list of users or roles that should be able to perform functions
# on these ECR repos. All other users and roles are to be forbidden.
# Formatted as 21 letters or numbers: AROAXXXXXXXXXXXXXXXXX or
# AIDAXXXXXXXXXXXXXXXXX -
# https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-unique-ids.
# Can be overridden on a per repo basis by the
# users_or_roles_to_allow_deny_all_else property in the repositories map.
default_users_or_roles_to_allow_deny_all_else = []
# A map of tags (where the key and value correspond to tag keys and values)
# that should be assigned to all ECR repositories.
global_tags = {}
# values to filter on when replicating the ECR repository to other regions.
# See
# https://docs.aws.amazon.com/AmazonECR/latest/userguide/registry-settings-examples.html
# for example values.
replication_filters = []
# List of regions (e.g., us-east-1) to replicate the ECR repository to.
replication_regions = []
}
Reference
- Inputs
- Outputs
Required
repositoriesanyA map of repo names to configurations for that repository.
Any types represent complex values of variable type. For details, please consult `variables.tf` in the source repo.
Details
Each entry in the map supports the following attributes:
OPTIONAL (defaults to value of corresponding module input):
- external_account_ids_with_read_access list(string) : List of account IDs that should have read
access on the repo. If omitted, use
var.default_external_account_ids_with_read_access.
- external_account_ids_with_write_access list(string) : List of account IDs that should have write
access on the repo. If omitted, use
var.default_external_account_ids_with_write_access.
- external_account_ids_with_lambda_access list(string) : List of account IDs that should have
access to create lambda functions with
container images in the repo. If omitted, use
var.default_external_account_ids_with_lambda_access.
- users_or_roles_to_allow_deny_all_else list(string) : List of users or roles that should be able to
access to perform functions on this ECR repo. All
other users and roles are to be forbidden. If ommitted,
use var.default_users_or_roles_to_allow_deny_all_else
- strict_deny_rules_enabled bool : Whether or not to enable strict deny rules on repo,
including deny on change repo policy. If ommitted,
use var.default_strict_deny_rules_enabled
- enable_automatic_image_scanning bool : Whether or not to enable image scanning. If
omitted use var.default_automatic_image_scanning.
- encryption_config object[EncryptionConfig] : Whether or not to enable encryption at rest for
the container images, and how to encrypt. If
omitted, use var.default_encryption_config. See
below for the type schema.
- image_tag_mutability string : The tag mutability setting for the repo. If
omitted use var.default_image_tag_mutability.
- tags map(string) : Map of tags (where the key and value correspond
to tag keys and values) that should be assigned
to the ECR repository. Merged with
var.global_tags.
- lifecycle_policy_rules list(object[LifecycleRule]) : List of lifecycle rules to apply to the ECR
repository. See below for the schema of the
lifecycle rule.
Structure of EncryptionConfig object:
- encryption_type string : The encryption type to use for the repository. Must be AES256 or KMS.
- kms_key string : The KMS key to use for encrypting the images. Only used when encryption_type is KMS. If
not specified, defaults to the default AWS managed key for ECR.
Structure of LifecycleRule object:
Refer to the AWS documentation on supported policy parameters:
https://docs.aws.amazon.com/AmazonECR/latest/userguide/LifecyclePolicies.htmllifecycle_policy_parameters
Example:
repositories = {
myapp1 = {
external_account_ids_with_read_access = ["11111111"]
}
}
Optional
Whether or not to enable image scanning on all the repos. Can be overridden on a per repo basis by the enable_automatic_image_scanning property in the repositories map.
truedefault_encryption_configobject(…)The default encryption configuration to apply to the created ECR repository. When null, the images in the ECR repo will not be encrypted at rest. Can be overridden on a per repo basis by the encryption_config property in the repositories map.
object({
# The encryption type to use for the repository. Must be AES256 or KMS.
encryption_type = string
# The KMS key to use for encrypting the images. Only used when encryption_type is KMS. If not specified, defaults to
# the default AWS managed key for ECR.
kms_key = string
})
{
encryption_type = "AES256",
kms_key = null
}
default_external_account_ids_with_lambda_accesslist(string)The default list of AWS account IDs for external AWS accounts that should be able to create Lambda functions based on container images in these ECR repos. Can be overridden on a per repo basis by the external_account_ids_with_lambda_access property in the repositories map.
[]default_external_account_ids_with_read_accesslist(string)The default list of AWS account IDs for external AWS accounts that should be able to pull images from these ECR repos. Can be overridden on a per repo basis by the external_account_ids_with_read_access property in the repositories map.
[]default_external_account_ids_with_write_accesslist(string)The default list of AWS account IDs for external AWS accounts that should be able to pull and push images to these ECR repos. Can be overridden on a per repo basis by the external_account_ids_with_write_access property in the repositories map.
[]The tag mutability setting for all the repos. Must be one of: MUTABLE or IMMUTABLE. Can be overridden on a per repo basis by the image_tag_mutability property in the repositories map.
"MUTABLE"Add lifecycle policy to ECR repo.
Any types represent complex values of variable type. For details, please consult `variables.tf` in the source repo.
[]Whether or not to enable strict deny rules on repo, including deny on change repo policy. Can be overridden on a per repo basis by the strict_deny_rules property in the repositories map.
falsedefault_users_or_roles_to_allow_deny_all_elselist(string)The default list of users or roles that should be able to perform functions on these ECR repos. All other users and roles are to be forbidden. Formatted as 21 letters or numbers: AROAXXXXXXXXXXXXXXXXX or AIDAXXXXXXXXXXXXXXXXX - https://docs.aws.amazon.com/IAM/latest/UserGuide/reference_identifiers.html#identifiers-unique-ids. Can be overridden on a per repo basis by the users_or_roles_to_allow_deny_all_else property in the repositories map.
[]global_tagsmap(string)A map of tags (where the key and value correspond to tag keys and values) that should be assigned to all ECR repositories.
{}replication_filterslist(object(…))values to filter on when replicating the ECR repository to other regions. See https://docs.aws.amazon.com/AmazonECR/latest/userguide/registry-settings-examples.html for example values.
list(object({
filter = string
filter_type = string
}))
[]replication_regionslist(string)List of regions (e.g., us-east-1) to replicate the ECR repository to.
[]A list of ECR actions to be denied.
A list of ECR actions to be denied (strict).
A list of IAM policy actions necessary for ECR read access.
A map of repository name to its ECR ARN.
A map of repository name to its URL.
A list of IAM policy actions necessary for ECR write access.